The pandemic has brought significant changes to technology management in companies from all sectors. This scenario has highlighted the importance of security with Zero Trust and VPNs in the new remote working model. In 2020, millions of workers around the world suddenly moved to the home office. This presented IT teams with urgent challenges. The main one was to guarantee secure and efficient remote access, even in “hostile” conditions, with employees connecting via the public internet and often using unprotected devices. Without these security solutions, many business operations could have been disrupted.
To understand the scale of this security challenge in remote working, a large technology company had to implement VPNs and Zero Trust solutions almost overnight. The measure involved around 140,000 employees in over a hundred countries. At the time, VPNs were the first choice for secure remote access. However, the concept of SASE and Zero Trust – an architecture that combines security, cloud computing and connectivity – was already under development and, with the pandemic, became more necessary than ever.
This situation showed that, although there were advanced technologies to deal with security problems in VPNs and Zero Trust, the biggest obstacle was speed of implementation. The new global reality has driven a change in mentality, leading companies to adopt more robust protection models, such as Zero Trust.
Never trust, always verify
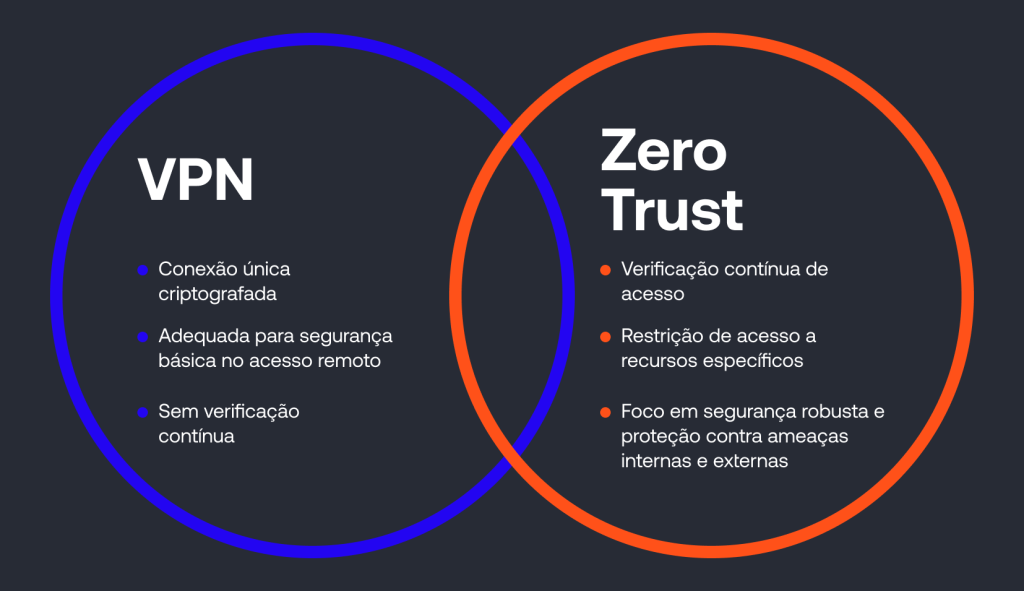
In addition, another emerging strategy for tackling these security challenges in remote working was Zero Trust, created by John Kindervag in 2010. In essence, the Zero Trust model is based on the principle of “never trust and always verify”. For this reason, it eliminates implicit trust in systems, requiring constant authentication to increase security. In practice, this approach limits users’ access to only the specific resources they need, which reduces the attack surface. As a result, the combination of Zero Trust and SASE has come to be used to protect network and cloud infrastructures against increasingly sophisticated threats, thus making the home office digitally secure.
Although Zero Trust has gained momentum, VPNs still have a role to play. Companies that need to offer secure remote access continue to rely on VPNs. These virtual private networks establish secure, encrypted connections between devices and corporate servers. This mechanism prevents attackers, using techniques such as packet sniffing, from intercepting information exchanged between users and the company network.
Differences between Zero Trust and VPN
From the point of view of cybersecuritythe main difference between VPNs and Zero Trust lies in how protection is implemented. While Zero Trust requires continuous verification for each access request, regardless of location, the VPN only encrypts the connection, without continuous monitoring. This distinction is essential because Zero Trust assumes that threats can come from inside or outside the network. In contrast, VPN is limited to protecting communication, leaving other layers of security to IT management.
One of the critical points of VPNs is latency. Encryption and data routing through remote servers can slow down the connection, impacting productivity. Even so, companies consider VPNs essential and can integrate them with the Zero Trust model and SASE infrastructure to create a layered security strategy, especially in the context of remote working.
Layered security for efficient remote working
With the transformation of remote work, Zero Trust reinforces security by focusing on customizable policies for identities and devices. Endpoint protection becomes essential, as external or outsourced workers often use shared or unmanaged devices, leaving them more exposed to threats. For these users, Zero Trust guarantees secure access to corporate resources, regardless of VPN use, by prioritizing continuous verification and visibility into user behavior.
In short, the pandemic was a milestone for the adoption of VPNs and Zero Trust in companies, providing robust security for remote work. By combining these approaches, IT teams are able to offer a secure and flexible remote working environment.
This content was produced by Huge Networks. Our company protects your corporate network, accelerates cloud applications, mitigates DDoS attacks and keeps cyber threats at bay. Subscribe to our newsletter and stay up to date with the latest news on security and digital infrastructure!
