The day-to-day life of Internet service providers in any country may seem tranquil, but it’s not. And yet, despite major difficulties rarely perceived by customers surfing the web, they manage to provide the means for everyone to connect to the network, at broadband speed and in an operation that rarely fails. This service may also seem quite simple. It simply receives data requests from the client device, transmits them to the destination servers and delivers the requested information to the client in response. But this tranquillity may seem the same as that of a cereal field seen from afar. Because of the distance, no one can see the insects, fungi, viruses and other pests that threaten the crops. In the same way, nobody sees the bad guys who carry out denial-of-service attacks against access providers.
Although these attacks are not visible, they are quickly noticeable. From one moment to the next, customers are no longer able to use any internet service. The cause of this type of failure is that in that time interval all the ISP’s servers are overloaded with meaningless requests. Requests sent by dozens and sometimes thousands of devices organized in an evil network called a botnet, sometimes created by the evildoer himself, sometimes rented to him to be used only for a few hours, in a very well-targeted attack. Internet providers are probably more vulnerable to DDoS attacks, which can affect the stability of networks and impair the user experience.
There are denial of service attacks all the time
There are websites on the Internet that show in graphs and tables, in real time, the data flows created by DDoS attacks. Anyone who knows them knows that these attacks happen all the time. And in practice there are no immune countries: every country in the world is both an origin and a destination. Some countries both generate and receive more data flows than others, such as China, the United States, Russia and even Brazil. The reasons for this lie in geopolitical issues. For example, trade wars and, more recently, war conflicts.
On these websites, you can see a very clear picture of the risk that these attacks pose to Internet providers. In the last ten years, according to statistics from major international network service providers, these attacks have used around 60 different strategies to target their victims. Each strategy is more efficient than the last. This forces telecom service providers to adopt more protection against DDoS attacks. How to change routes, block source addresses, change firewall rules, among other measures.
Although we have generically referred to the perpetrators of the attacks as “evildoers”, they do not all fit into a single category, as they are motivated by a variety of different reasons. There are everything from attacks on access providers to extort money to attacks by cyber-activists in the name of some cause they defend. It is already predicted, for example, that next month, July 2024, French organizations will be bombarded with this type of attack simply because France is hosting the Olympic Games. Attacks such as those that took place in Brazil during the 2014 World Cup and the 2016 Olympics. Cyber-activists who don’t like France or the French are going to take action with DDoS attacks.
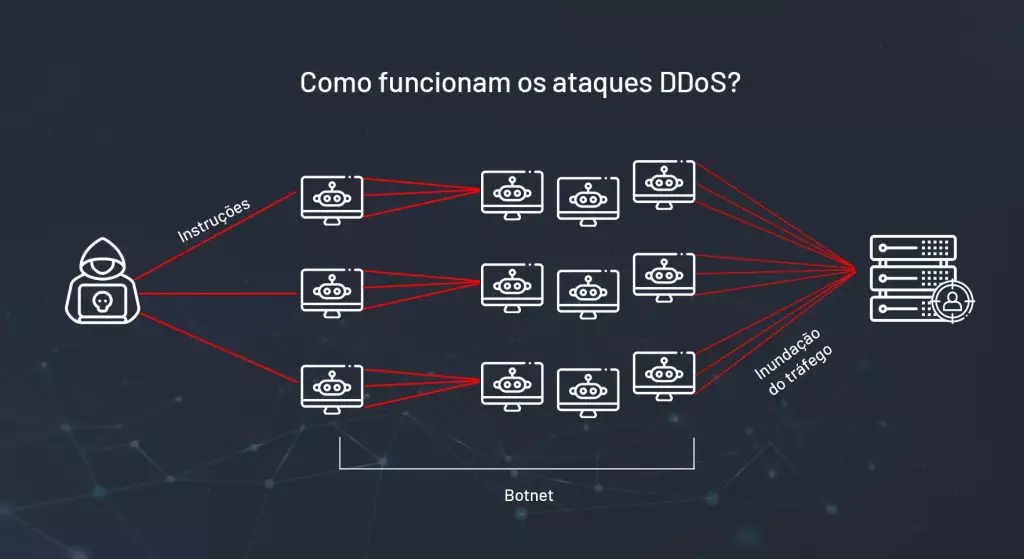
The right strategies against DDoS attacks
But since denial-of-service (DDoS) attacks have been around for a long time, telecommunications and network service providers are well aware of them and, because of this, have various ways of mitigating them. Currently, cloud-based solutions are recommended by them as the most efficient, especially because of the quantity and elasticity of the resources available. Of course, any company has the option of acquiring and managing local solutions, but they end up being expensive not only in terms of equipment, but also in terms of labor. You need specialists to manage all the equipment at all times.
Companies specializing in this type of service, such as Huge Networks, invest in state-of-the-art equipment. In addition, they devote significant resources to researching and developing specific software for handling malicious traffic. And since there are already high-volume attacks, at some point they could exhaust the local mitigation capacity installed in a company. From that point on, the solution will consist of diverting all traffic into a “black hole”. This achieves the attacker’s goal – the company will be isolated from the Internet, without receiving any traffic. Internet providers therefore need to be one step ahead in order to mitigate DDoS attacks effectively.
Everyone knows: cheap is expensive
In an ISP, this would be a disaster. Crooks have frequently attacked small and medium-sized Internet service providers in Brazil, hoping to get some kind of cash payment from them to stop the attack. Since these attackers know how much mitigation services cost, they always ask for a little less than that as a “ransom”, assuming that the victims will prefer to pay the ransom in order to save money.
Fortunately, Brazilian providers have become aware that cheap is expensive and are increasingly looking for professional solutions. This evolution has been stimulated by organizations such as Abrint, the Brazilian Association of Internet and Telecommunications Providers, which already brings together more than two thousand providers in the country. And by the companies that provide the most advanced security solutions for telecommunications. Like Huge Networks.

