Ransom DDoS, a digital threat that combines denial of service and extortion, is emerging as an increasingly significant and growing challenge in the cyber world. This complex phenomenon, which uses the interruption of online services as a bargaining chip, brings with it nuances that deserve in-depth analysis.
In this article, we will explore the complexities of RDDoS, tracing its evolution from the earliest records to the modern tactics carried out by contemporary cybercriminals.
RDDoS: you never know when this attack will happen
Few cybercrimes have been as damaging as ransomware. Although it’s not new, this type of crime has wreaked havoc all over the world, affecting everything from small businesses to global corporations: cybercriminals contaminate computers and demand a sum of money to reverse the situation.
On February 21 of this year, one of these attacks hit Change Healthcare in the United States, a company responsible for processing health insurance documentation (prescriptions, certificates, charges, payments, transfer of funds and much more). As the company processes data for around half of the health plans, the losses in the sector have already appeared and many clinics and laboratories have warned the market that they are running out of cash, and in some cases will have to resort to bank loans to make ends meet.
The attack could have started in several ways – there could have been a phishing contamination (in this case, malware received in an email, for example) or an intrusion into the network through a vulnerability in one of the devices connected to it. But there is an extortion attack, in which the cybercriminal also demands a ransom, and in which none of this is necessary: he doesn’t need any malware for his actions, and can attack remotely with RDDoS – or Ransom DDoS, a denial of service attack with a ransom demand, which is sent by email. Companies that are not protected by a good malicious traffic mitigation service can consider themselves at risk.
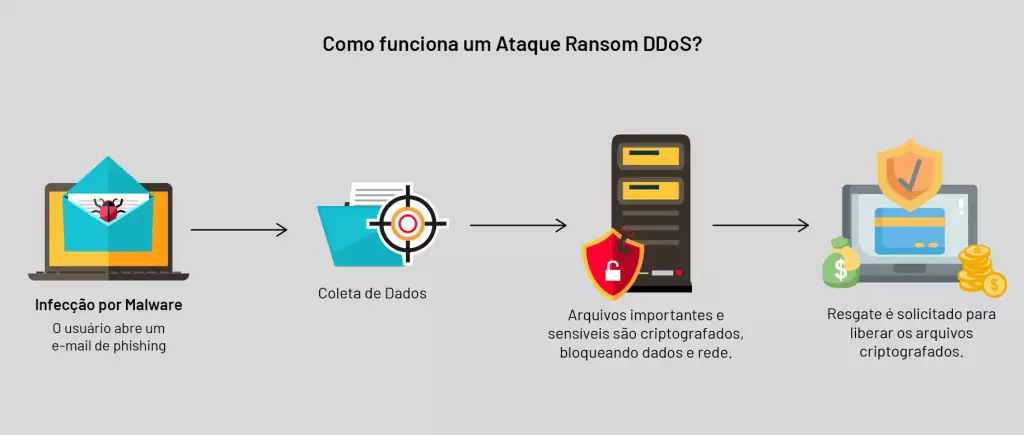
DDoS is already offered as a service
RDDoS developed with the emergence of the rental of attack platforms – this rental became known as DDoS-as-a-Service and multiplied the interest of criminals in obtaining almost immediate gains at a very low cost and risk.
Storm, in 2007, was one of the first botnets to offer attacks as a service: the network had between 250,000 and 1 million devices and could be rented by anyone. Some of its servers were shut down in 2008 and it gradually became inactive. Since then, the DDoS as a service model has allowed gangs with basic technical skills (or none at all) to launch heavy attacks on their victims.
It can be said that it is practically impossible to determine when and where such an attack will take place: although law enforcement authorities around the world monitor the dark web for clues on this subject, it is rare to see news that a person has been arrested on charges of having carried out or planned a DDoS attack, with or without a ransom demand.
Most frequently, the platforms selling the service are discovered and taken down. These platforms control one or more botnets and activate them against one or more Internet addresses when their services are contracted.
A difficult problem for the authorities
No matter how hard authorities in all countries work to combat cybercriminals and their resources, such as servers, platforms and domains, they are constantly organizing new botnets and installing new platforms to sell attack services. One of the main reasons for this is that there are many people looking for these services, both on the dark web and on the surface of the Internet.
One of the main attractions of these new cybercriminals is that they don’t have to spend much to gain access to the firepower of these cyberweapons. Last year, a survey by cybersecurity company Searchlight Cyber revealed an increase in the availability and number of people interested in these platforms, called “stressers” and “boosters”.
One of them, “Nightmare Stresser”, which has been operating since 2020, already had more than 566,000 registered users and 52 servers, and could carry out attacks using 28 different methods, divided into three broad categories: Layer 4 (Transport) UDP, Layer 4 (Transport) TCP and Layer 7 (Application) TCP. Another platform studied in the survey, called Paper Stresser, used 12,000 bots to conduct the attacks and could fire up to 700 GB/s.
The service was offered in four different monthly subscription amounts, ranging from $30 to $125, promising attack intervals of up to 500 seconds with 18 different methods. There are platforms that offer monthly services with subscription prices ranging from $30 a month to $18,000 a quarter. The most expensive option offers unlimited attacks per day and an attack duration of up to two hours, with one hundred simultaneous attacks.
Three days of RDDoS attacks
One of the most serious RDDoS attacks began on October 21, 2022 and only ended two days later: the victims were eight companies that offer secure email and other privacy and security services – Runbox, Posteo, Fastmail, TheXYZ, Guerilla Mail, Mailfence, Kolab Now and RiseUp. They all received an email asking for a ransom of 0.06 BTC (around US$4,000 at the time).
The companies were given three days to pay, and the attackers threatened to take their networks offline if they didn’t pay. The same thing has been happening to small and medium-sized ISPs in Brazil – they are attacked with DDoS and receive emails demanding payment to stop the attack.
Although the problem is not new, there is no sign of it disappearing: it can arise at any time, with varying intensity and duration, but always with the same demand: money. Although many victims have already paid up, they know that this is not the solution and that other attacks will still happen. The solution lies in investing in technology, hiring partners who know the subject well, such as Huge Networks, and who have the resources to filter traffic and protect customers from attacks like these.